Blog
Expert insights on AWS, DevOps, and Security
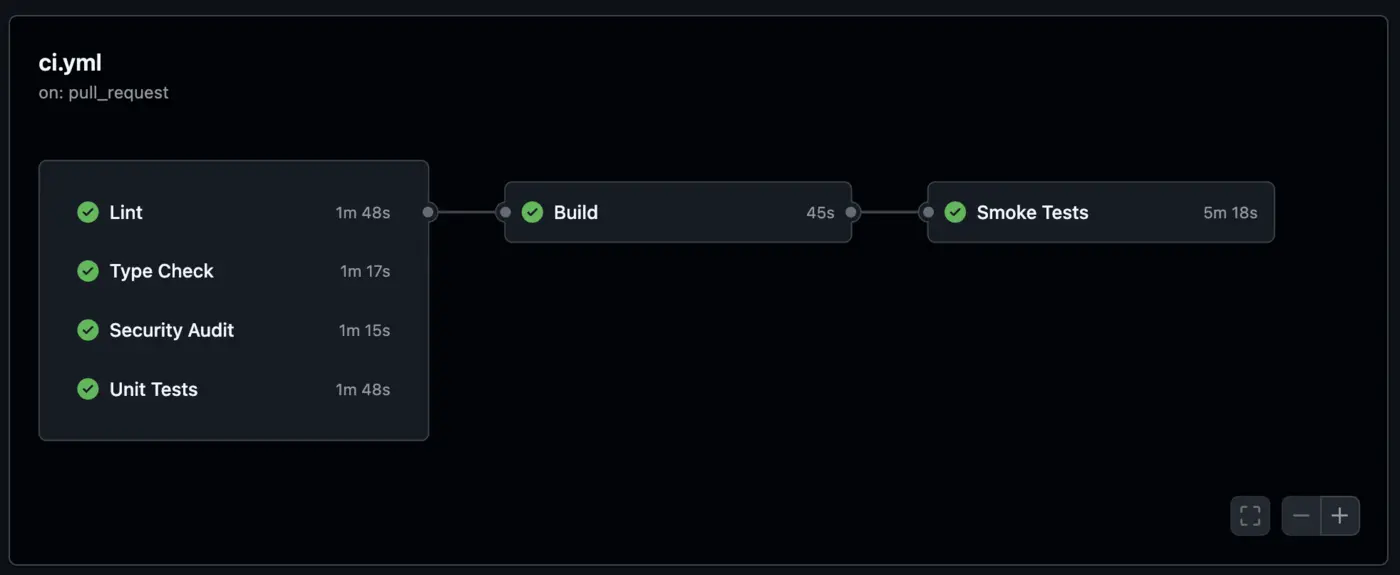
Beyond GitHub Actions Quota Limits: Building Production-Grade CI/CD Artifact Storage
When GitHub Actions quota limits halted a startup's entire deployment pipeline for 24 hours, we helped them build a strategic solution. Learn the decision framework for evaluating artifact storage, why most teams make the wrong architectural choices, and how to build CI/CD infrastructure that scales with your business.

Introducing zxtra: Our AI Assistant Built on Cloudflare Workers AI
We built zxtra, an AI assistant that answers questions about ZSoftly directly on our website. Learn how we used Cloudflare Workers AI to create a fast, secure chatbot with zero infrastructure overhead.
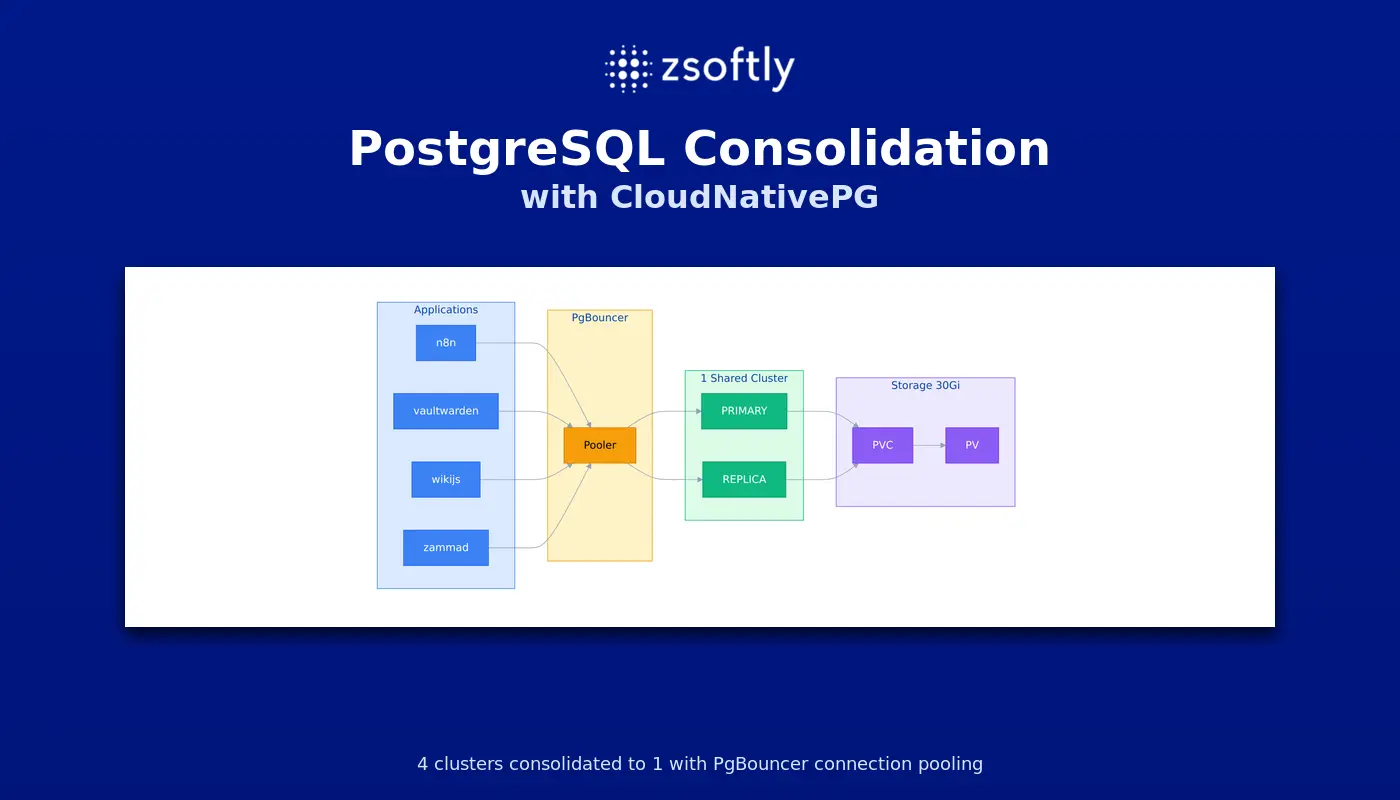
How We Consolidated 4 PostgreSQL Clusters into 1 with CloudNativePG
We ran 4 separate PostgreSQL clusters for 91MB of data. Each cluster had its own PodDisruptionBudget blocking node drains. This guide shows how we consolidated them into a single HA cluster with PgBouncer connection pooling using CloudNativePG and ArgoCD.

Cloud Security Compliance Automation Costs in Canada
Learn how Canadian businesses can use cloud security compliance automation for SOC 2, HIPAA, and ISO to cut risk, reduce audit pain, and control long-term costs.
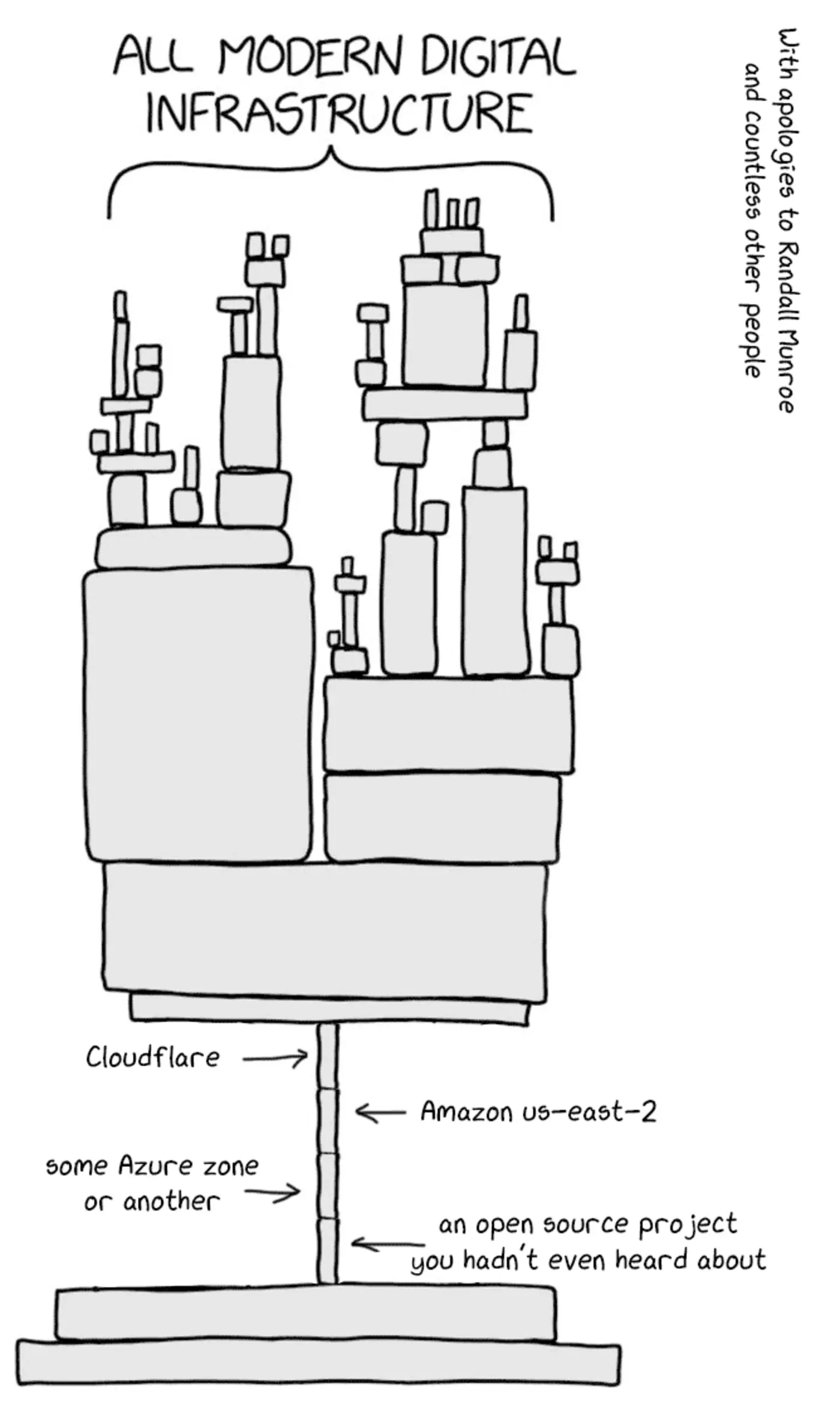
Why Hybrid Cloud is the Future: A Complete Guide After the 2025 Outage Crisis
After four major cloud outages in a 30-day period (AWS, Azure, GitHub, Cloudflare), 80% of enterprises are moving to hybrid cloud. This comprehensive guide covers the concentration problem, SaaS dependency risks, the business case for hybrid cloud, and a practical 8-step implementation playbook.

Building a Secure Cloud Infrastructure: The Essential AWS Security Stack for Mid-Market Companies
Multi-layered security approach including CloudWatch monitoring, CloudTrail auditing, and AWS Config compliance. Phased implementation roadmap with budget considerations, automation scripts, and IaC templates to achieve compliance without dedicated security teams.

Kubernetes FinOps for Growing Companies: From Chaos to Cost Control
Establish standardized labeling conventions for cost attribution, implement cost budgets at team level, and automate resource cleanup. Includes practical templates for TTL policies and integration with existing DevOps workflows.

Multi-Cloud CSPM Implementation: Managing AWS, Azure, and GCP Security from a Single Pane of Glass
AWS has 15,000+ IAM actions, Azure nearly 19,000, and GCP over 10,000. Learn practical approaches for unified security monitoring, compliance automation for GDPR, HIPAA, and SOC 2 without enterprise-grade tools.

The Mid-Market DevSecOps Playbook: Integrating Security into Your CI/CD Pipeline Without Breaking the Bank
Integrate SAST, DAST, and secret scanning into your CI/CD pipeline using open-source alternatives to expensive security tools. Step-by-step implementation guide with GitLab CI/CD, AWS CodePipeline, and ROI calculations for security automation.

AWS Secrets Management Simplified: Choosing Between Secrets Manager, Parameter Store, and AppConfig
AWS offers three services for secrets and configuration management. Learn when to use Secrets Manager for secrets, Parameter Store for simple key-value pairs, and AppConfig for feature flags. Includes cost comparison, migration strategies, and CloudFormation templates.
GitOps + Kubernetes Cost Optimization: Reducing Cloud Spend by 80% Without Sacrificing Performance
Spot instances can cut compute costs by up to 90%. Learn actionable strategies for SMBs running Kubernetes, including GitOps-driven resource right-sizing, cost visibility in CI/CD pipelines, and real-world examples of dramatic cost reductions.

Zero-Trust Access with AWS SSM: Eliminating SSH Keys and Bastion Hosts Forever
Learn how AWS Systems Manager Session Manager enables secure access without SSH keys, open ports, or bastion hosts. Includes practical IAM policy templates, cost savings analysis, and complete migration strategy from traditional SSH to SSM-based access.

Cloud Security Posture Management (CSPM) for SMBs: How to Achieve Enterprise-Grade Security on a Mid-Market Budget
Learn how mid-market companies ($10M-$100M revenue) can achieve enterprise-grade cloud security at 20% of the cost using AWS native tools. Includes practical implementation roadmap, cost breakdowns, and proven strategies for CSPM implementation without dedicated security teams.

Bypassing VPN Failure with AWS SSM Port Forwarding
A real-world scenario demonstrating how to maintain secure access to critical servers when VPN fails. Learn how AWS SSM Port Forwarding provides out-of-band emergency access for Windows and Linux servers through secure tunneling.

How AWS Route53 Profiles Solved DNS Challenges in SMB, Corporate, and Startup Environments
Real-world case studies showing how Route53 Profiles transformed DNS management for organizations of all sizes. Learn how to centralize DNS configurations across multiple AWS accounts and VPCs, eliminating complexity and ensuring consistent, secure access to critical resources.